IBM Consulting unveils Center of Excellence for generative AI
IBM Journey to AI blog
MAY 25, 2023
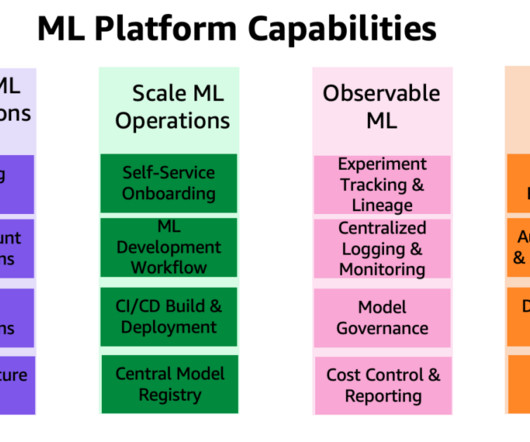
It stands alongside IBM Consulting’s existing global AI and Automation practice, which includes 21,000 data and AI consultants who have conducted over 40,000 enterprise client engagements. At the same time, there are reasonable concerns about how to mitigate bias, manage data security, and factor in precision and risk.




























Let's personalize your content