5 Steps to Integrate IoT with CRM for Small Businesses
Aiiot Talk
MAY 18, 2024
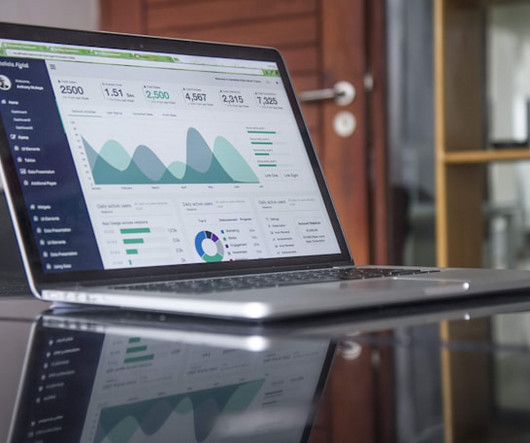
Determine What Data You Need “While it’s true that more data leads to higher accuracy, too much information can make it hard to hone in on what’s most impactful.” While the IoT can collect a wide range of information — experts believe IoT devices will generate 79.4 zettabytes of data by 2025 — not all data points are equally valuable.






































Let's personalize your content