Empowering security excellence: The dynamic partnership between FreeDivision and IBM
IBM Journey to AI blog
MAY 8, 2024
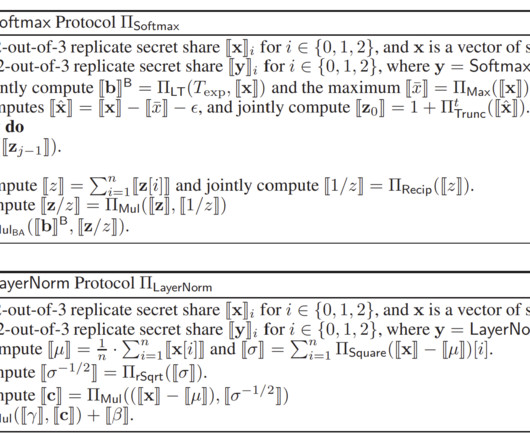
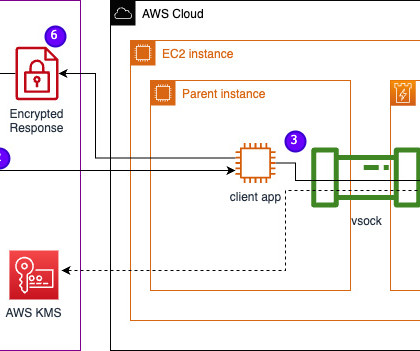
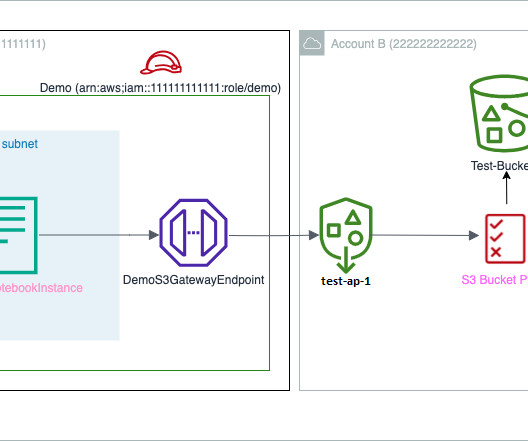
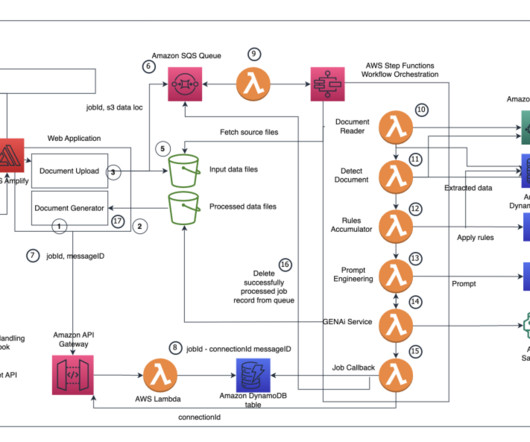
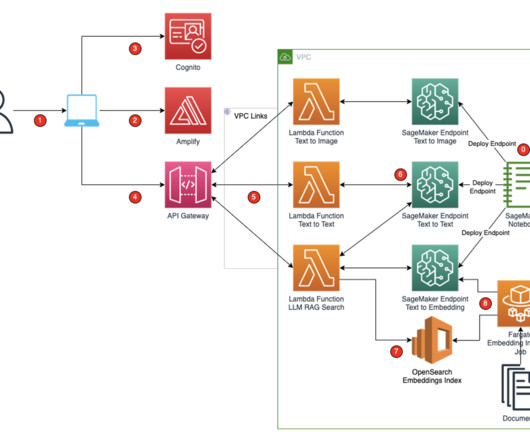
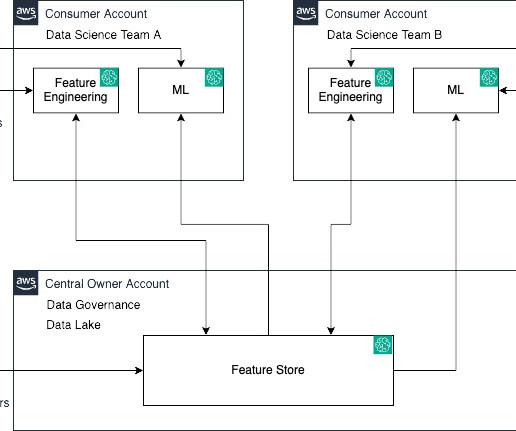
Operating as a security service partner, FreeDivision leverages IBM’s endpoint detection and response (EDR) solution, IBM Security® QRadar® EDR, as part of its solution, freedivision.io, to address the unique security concerns of its clients. Unfortunately, it turns out that this alone was not enough.




































Let's personalize your content