Data protection strategy: Key components and best practices
IBM Journey to AI blog
MAY 28, 2024
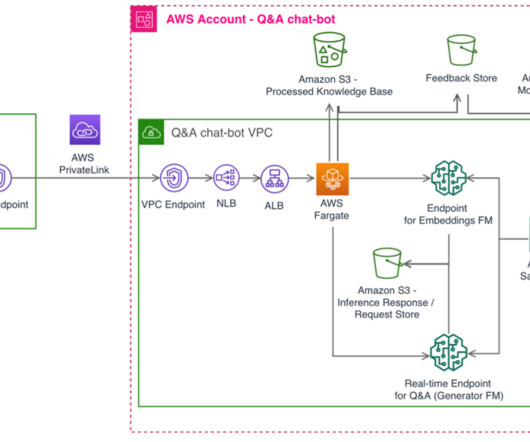
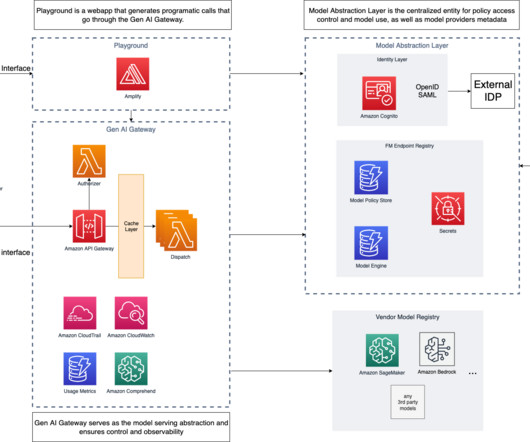
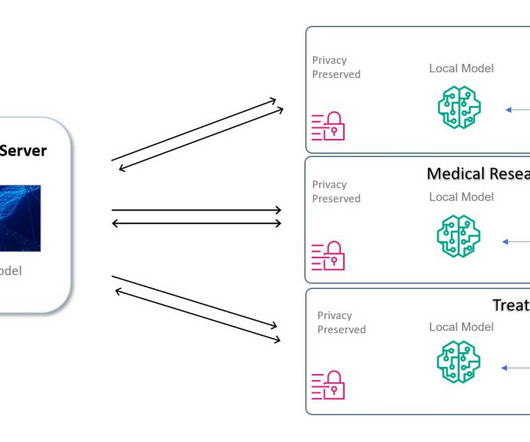
While every data protection strategy is unique, below are several key components and best practices to consider when building one for your organization. It can also help them reduce vulnerabilities and ensure data is efficiently managed, compliant with regulations, and not at risk of misuse or loss. What is a data protection strategy?



































Let's personalize your content