5 Steps to Integrate IoT with CRM for Small Businesses
Aiiot Talk
MAY 18, 2024
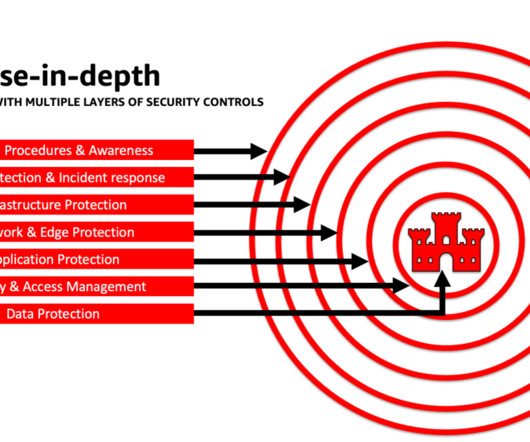
Compare IoT and CRM Platforms You can compare available solutions after deciding on an IoT use case and general data categories. Secure Your IoT Data “IoT endpoints often lack strong built-in protections and can provide an easy way for cybercriminals to jump to more sensitive devices and data.”






























Let's personalize your content